Microsoft Defender ATP & Configmgr CMPivot with a CMG (Cloud Management Gateway) better together; How we saved the customer from Emotet related malware
In September 2018, one of our customers was targeted by a phishing attack in attempts to infiltrate malicious code on their systems. These attempts were successful and a widespread Emotet-related malware attack followed. This is the story on how we countered and contained it with the use of Configuration Manager CB 1806 and CMPivot. One of the tricky parts was that most workstations where still Windows 7 and Windows 7 embedded. Only 20% was native Windows 10 1709.
The phishing email was well disguised and was made to believe it originated from a corporate director. The content of the email suggested that invoices had not been paid and requested the addressee to open attached Excel or PDF file and follow up. This was convincing enough to some, who indeed opened the files and clicked on whatever links or “Enable content” messages held within. This triggered the seemingly random creation of executables on the local system, which in turn contacted Command & Control servers to download further payloads.
First signs of infection came on a Tuesday, through SCCM Endpoint Protection alerts: 5 infections of an Emotet-related strain, which were all quarantined. This was reported to the Security Team lead, with no further actions other than following up on more infection alerts, if any. On Wednesday, there were about 25 reported infections and we were actively investigating.
We used the (at the time) new CMPivot feature in SCCM CB 1806 to detect malware-generated executable files which served to contact C&C and download payloads. Through SCCM Endpoint Protection, we learned there was a pattern in the filenames and the locations where they were created. Some of these executables were used to create services which ran under SYSTEM context. We then triggered PowerShell scripts on the detected systems, to stop and disable those services and to move malicious files to a holding locations. This approach rendered the files harmless, while still allowing to collect and investigate them further. We also wanted to report on systems where users had non-authorized local admin rights.
These are the queries we used in CMPivot:
Process | where ((CommandLine like ‘%system32//%.exe’) or (CommandLine like ‘%syswow64//%.exe’))
Process | where (CommandLine == ‘”C:\\Windows\\system32\\volumebundle.exe”‘)
Process | where (CommandLine == ‘”C:\\Windows\\system32\\volumebundle.exe”‘) | where (CreationDate == ‘2018-09-14 06:41:00’)
Process | where (CreationDate like ‘2018-09-14 06:41:00’)
File(‘%public%\\*.exe’)
Administrators | where (ObjectClass == ‘User’) | where (not (Name like ‘%Admin%’))
If wanted we can deliver the PS script to mitigate infections.
That same day, the Network & Security team reported a lot of C&C related activity being picked up by the CheckPoint firewall. In the days following, the outgoing traffic was monitored and firewalls kept most, if not all suspicious traffic contained. Malware infections kept spreading however and the phishing attack was still going as well. Teams were informed and staff was instructed to not open any suspected emails.
First reports came is that users had received alerts from cloud services that their credentials had been compromised. For instance, Google accounts had been used to login from IP addresses throughout the world. These credentials had been stored on the users’ computers in browser password managers.
That Wednesday evening, a crisis meeting with corporate management was held and reactive measures were discussed. The only real actions we felt we could suggest, was to cut off internet access for the time being and to shut down SMB v1 services. The first would impact business-customer productivity and was denied. The latter would severely impact business productivity as most file servers and legacy applications still used SMB v1. This suggestion was also denied. For reference: there had been a WannaCry-related attack the year before, where SMB v1 was cut off by the IT teams to prevent the attack from spreading further, which was promptly overruled by business the next day, accepting the risk of the malware spreading, in fact waving away the risk as overrated. Luckily, no files or systems were encrypted then.
On Thursday, we proposed to implement Windows Defender ATP, however, another service provider implemented Sentinel One implementation. It did not go well as prerequisites were not advertised installed correctly. Windows Embedded was not mentioned as not being supported, AFTER the wide spread deployment of SentinelOne agents through SCCM application deployment. Furthermore, despite SentinelOne actively detecting and stopping many malware strains, infections were still spreading and firewall kept picking up C&C traffic.
In the meantime, the proposed WDATP PoC was setup and agents were onboarded. However, it clashed with the still present SentinelOne agents, reporting it as malware and rendering slower systems unusable due to the high usage of CPU resources. We finally found a method to uninstall SentinelOne agents. Again, we used CMPivot to detect and intervene on systems where this issue occurred. The results were used to create a device collection to deploy the uninstall method to.
These are the queries we used in CMPivot:
EventLog(‘System’) | where (EventID == 7031) and (Message like ‘%Sentinel%’)
EventLog(‘System’) | summarize countif( (Message like ‘The Sentinel Agent service terminated unexpectedly.%’) ) by Device | where (countif_ > 0)
The cleanup of SentinelOne was mostly successful through these methods, leaving some systems to be reinstalled completely.
ATP onboarding was successful and immediately, new malware infections were reported and contained, including strains the other product had not detected.
In the end, there were no confirmed reports of data breaches other than some users personal credentials having been stolen from browser password managers.
WDATP was purchased after a positive evaluation and thanks to Microsoft’s technical and commercial approach in supporting the deployment and CMPivot was a great addition to react when we where out of control.
If you want to look at Microsoft Defender Advanced Threat Protection , please do not hesitate to contact us at info@ob-v-us.be
Best Regards ,
The workplace & security team.
Meet the Belgians at MMS DE !
- Opening with MMS 2018 Desert Edition Welcome Reception – That will be hilarious
- Monitoring Configmgr
- Patch management with log analytics! Best of both worlds?
- Enterprise Mobility Suite Part 1 & 2

MVP Enterprise Mobility
Update KB4343909 for Windows 10 1803 kills Windows Defender Application Guard
Update KB4343909 for Windows 10 1803 has broken ‘Windows Defender Application Guard’ (WDAG) after installing the August 2018 KB4343909 update.
The Windows Defender Application Guard reports the error code 0xC0370106 as shown below.

We confirm that it is a ‘known issue’ if you read the release notes of KBb4343909 : “Launching Microsoft Edge using the New Application Guard Window may fail; normal Microsoft Edge instances are not affected.”
The workaround is uninstall the KB4343909 update and install updates KB4340917 and KB4343909 in that specific order. Microsoft will fix this in the September release.
Kenny Buntinx
Hybrid Mobile Device Management (MDM) and why you should plan for migration now !
Hi ,
Microsoft recently posted a service change announcement in the Office Message Center to customers using Hybrid Mobile Device Management (MDM). Maybe you are one of those type of customers that need to take action as you are using SCCM + Intune in hybrid mode and this impacts you .
MC146431 – Plan for Change: Move to Intune on Azure for your Mobile Device Management
Since launching on Azure over a year ago, Intune has added hundreds of new customer-requested and market-leading service capabilities, and now offers far more capabilities than those offered through hybrid Mobile Device Management (MDM). Intune on Azure provides a more integrated, streamlined administrative experience for your enterprise mobility needs.
As a result, we see that most Enterprise Mobility + Security (EMS) customers choose Intune on Azure over hybrid MDM. The number of customers using hybrid MDM continues to decrease as more customers move to the cloud. Therefore, on September 1, 2019, we will retire the hybrid MDM service offering.
Note: This change does not affect on-premises System Center Configuration Manager (ConfigMgr) or co-management for Windows 10 devices.
Please plan your migration to Intune on Azure for your MDM needs. OB-V-US has tools and other resources to help you with this migration.
Best Regards ,
Kenny Buntinx
MVP in Enterprise Mobility – 10th Anniversary.
I’m very proud to announce that my MVP award got renewed for the year 2018 – 2019 in the category of Enterprise Mobility and at the same time it is also my 10th anniversary.

This is certainly a great honor for me and our company OB-V-US.
Thank you Microsoft, Blog readers and all the community members that helped me out!
Thanks for the recognition. I am delighted.
Kenny Buntinx
Enterprise Mobility MVP
Upgrading from ConfigMgr 1702 to 1706 gives you “Microsoft SQL Server reported SQL message 2627, severity 14” in your status messages
If you upgraded your ConfigMgr 1702 or earlier environment to Configmgr 1706 and in the status messages after the upgrade you get :
Microsoft SQL Server reported SQL message 2627, severity 14: [23000][2627][Microsoft][SQL Server Native Client 11.0][SQL Server]Violation of PRIMARY KEY constraint ‘SUM_DriverUpdates_PK’. Cannot insert duplicate key in object ‘dbo.SUM_DriverUpdates’. The duplicate key value is (d8483f4f-0390-49db-b251-faf884dd8eaf
Be aware that the Product Group are aware of this issue and are on a working on a fix. The result of this problem is that admins cannot see new Surface driver updates.
Other than that, nothing else is impacted so it can be ignored.
Hope it helps ,
Kenny Buntinx
MVP Enterprise Mobility
Enterprise Mobility : In the land of NDES – Where one eye is King and you need to watch your CRL Delta files
I was doing a EMS POC and deployment of certificates on mobile devices was a requirement. So I needed to setup an NDES server with a separate Subordinate CA for MDM , NDES Server and SCCM Certificate Registration Point (CRP). Big deal I thought as I did it a already multiple times. At my customer we worked close with the server team and setup the infrastructure which was working fine at first sight.
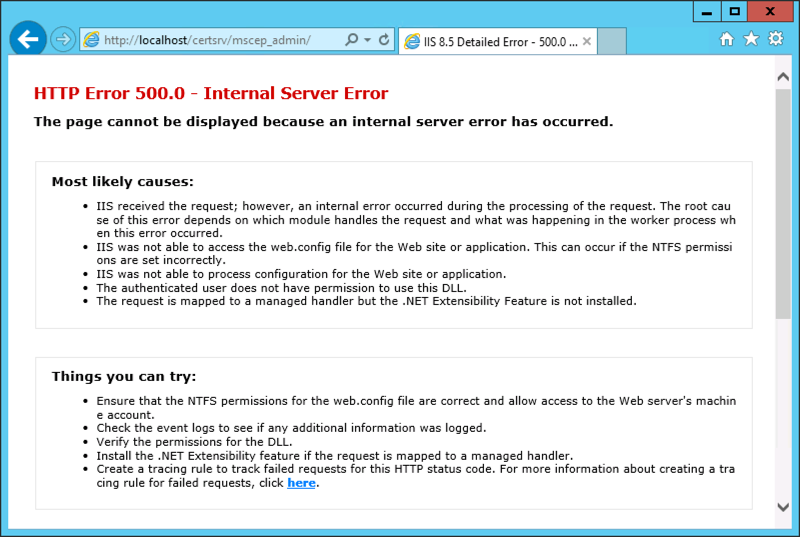
After a reboot of the NDES server I was struggling to get the Network Device Enrollment Service (NDES) up and running again as it would throw me an error 500.
The event log of the NDES Server told me the following:
The Network Device Enrollment Service cannot retrieve one of its required certificates (0x80070057). The parameter is incorrect.
The Network Device Enrollment Service cannot be started (0x80070057). The parameter is incorrect.
When the service starts, it searches for two certificates that are used by the service :
1. The service searches in the machine MY store AND
2. The certificate must have the following extensions AND
For the Key Exchange certificate:
– ExtendedKeyUsage: “Certificate Request Agent”
– KeyUsage: Encryption (0x20)
For the enrollment agent certificate:
– ExtendedKeyUsage: “Certificate Request Agent”
– KeyUsage: Signature (0x80)
3. The certificate must not be archived AND
4. The computer must have the private key for the certificate AND
5. The certificate must be issued by the same CA that the service is configured for AND
6. The certificate must have a valid chain AND
7. If there is more than one certificate for either of the certificates that meets the previous criteria, the service will select the most recent one (the latest that was issued)
Troubleshooting certificate issues will require you to enable the CryptoAPI 2.0 Event Logging :
The CryptoAPI 2.0 Diagnostics is a feature available from Windows Server 2008 that supports the trouble shooting of issues concerned with:
– Certificate Chain Validation
– Certificate Store Operations
– Signature Verification
Enable CAPI2 logging by opening the Event Viewer and navigating to the Event Viewer (Local)\Applications and Services Logs\Microsoft\Windows\CAPI2 directory and expand it. You should see a view named Operational.Next, right-click on the Operational view and click the Enable Log menu item.
Searching the right information under the capi2 operational log :
I was quite sure, that I was able to download the CRL (Certificate Revocation List) and I double checked that by browsing to the URL ‘.crl”>http://pki.xxx.be/CertEnroll/<NameOfYourSubCA>.crl’ and I was able to download the file. When digging deeper in the eventID’s , I found at EventID 42 , the following URL ‘.crl”>http://pki.xxx.be/CertEnroll/<NameOfYourSubCA+>.crl’ was shown. This means it was looking for the availability of the Delta CRL, which was visible on the web site of my CRL:
When I finally tried to download this CRL Delta file, it failed. I remembered myself, that IIS is treating the + sign very differently in URL’s.
I needed to set the setting “Allow double escaping” in the web.config file as shown below :
After enabling this, NDES was able to retrieve the Delta CRL file and start the service gracefully.
So if your NDES Server is throwing “The Network Device Enrollment Service cannot retrieve one of its required certificates (0x80070057). The parameter is incorrect.”, do not only check your certificates on the Server, check also your CRLs and Delta CRLs!
Hope it Helps,
Kenny Buntinx
MVP Enterprise Mobility
When deploying Windows Server 2012R2 using an Configmgr OSD Task Sequence, additional disks will be offline when the Task Sequence completes
When using a Configuration Manager OSD Task Sequence to deploy Windows Server 2012 or Windows Server 2012 R2 to a server (VM) that contains disks that are not local (such as SAN Disk), when the Task Sequence completes, the additional disks may not come online and may show as offline. Specifically in the Disk Management, the additional disks will show offline with the message:
Disk is offline due to a policy set by an administrator
If you look at my VM, you will see I have 2 separate disks that I will need in a later phase to install the backup software to the D:\ partition, residing on the other vmdk.
To resolve the issue, for the WinPE phase, the steps from KB971436 need to be added to the Task Sequence. For deployments from Operating System Images, a registry key value will need to be updated with the correct SAN policy value as shown below:
Just after the step where you apply the image, create a “RunCommand line called :”load system hive” and execute :” reg load HKUtemp "%OSPART%\WindowsSystem32ConfigSystem"”
Just after the step where you apply the “RunCommand line called :”load system hive”, create a “RunCommand line called :”Change Default SAN policy” and execute :”reg add HKUtempControlSet001HKLMSystemCurrentControlSetServicespartmgrParameters /v SanPolicy /t REG_DWORD /d 1 /f”
Just after the step where you apply the “RunCommand line called :”Change Default SAN policy”, create a “RunCommand line called :”Unload system hive” and execute :”reg unload HKUTEMP”
Next phase is to make sure that no drives will remain offline and all drives will still have the right driveletters assigned . Run a command line with : diskpart /s diskpart.txt
The contents of the diskpart.txt can be determined by yourself . Here is an example
Hope it Helps ,
Kenny Buntinx
MVP enterprise Client Management